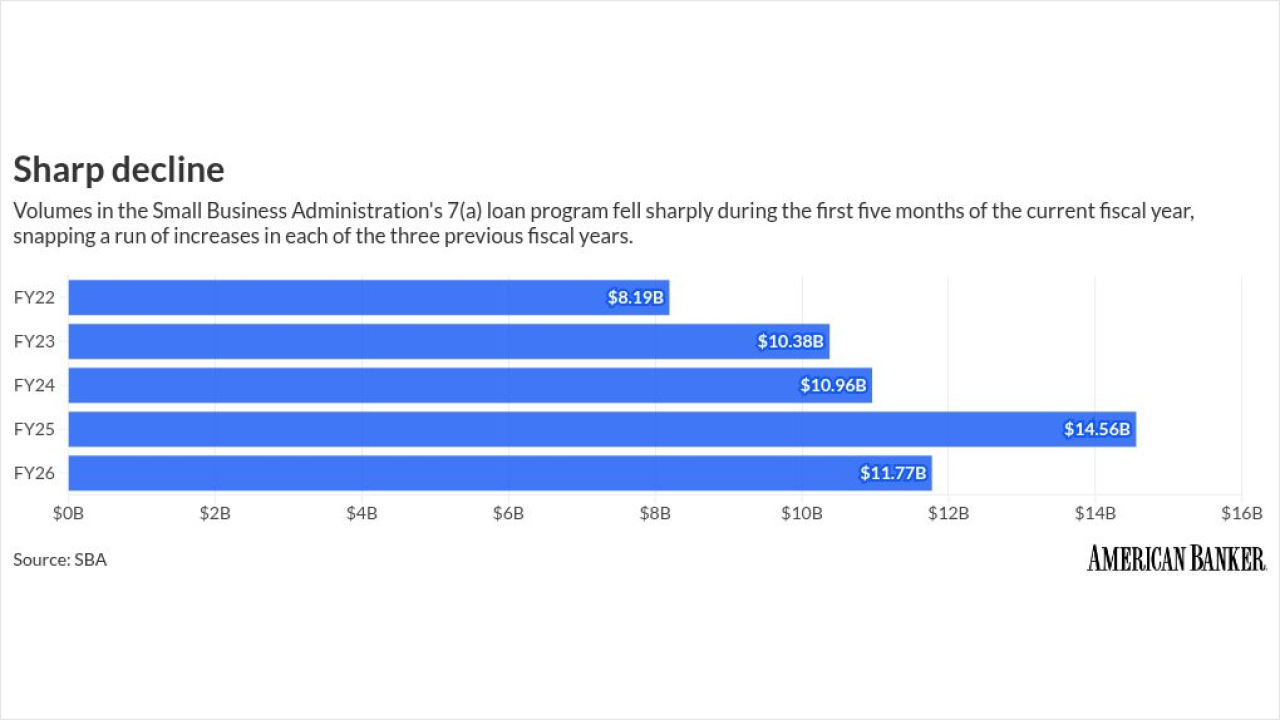
Ransomware attackers threatened to extort $866 million from U.S. bank customers last year in a record-breaking scourge primarily perpetrated by threat actors affiliated with Russia.
The Financial Crimes Enforcement Network, a bureau of the Department of the Treasury, released the information in
The $866 million in threatened extortions stem from 1,251 reported incidents that occurred in 2021. FinCEN said it received an additional 238 reports in 2021 regarding incidents that occurred in 2020 or earlier. The total value of payments banks reported in ransomware-related suspicious activity reports in 2021 was $1.2 billion.
Fincen did not draw a conclusion about whether the increase in reported incidents reflected an increase in actual ransomware-related incidents or improved reporting and detection.
Regardless, the data shows financial institutions play a critical role in helping to protect the U.S. from ransomware-related threats "simply by fulfilling their Bank Secrecy Act compliance obligations," according to Himamauli Das, Fincen's acting director.
"Today's report reminds us that ransomware — including attacks perpetrated by Russian-linked actors — remains a serious threat to our national and economic security," Das said. "It also underscores the importance of BSA filings, which allow us to uncover trends and patterns in support of whole-of-government efforts to prevent and combat ransomware attacks."
The bureau said it performed data cleansing before disclosing the figures, to remove duplicated reports that cover the same incidents. However, Fincen said in the report that "filings on the same incident from different financial intermediaries are highly valuable for investigative purposes." Multiple filings regarding the same incident also illustrate reporting compliance, it said.
Three-quarters (75%) of ransomware-related incidents in 2021 likely emanated from (or at a minimum were connected to) Russia, according to Fincen. Each of the five highest-grossing ransomware variants during that period also showed ties to Russia. Fincen identified the highest-grossing ransomware variant, which it did not name in the report, in 124 incidents totaling $84.2 million in value.
According to
Investigators established links to Russia by determining that the ransomware had Russian-language code, that it was programmed not to attack targets in Russia or post-Soviet states, or that threat actors advertised the ransomware primarily on Russian-language sites.
For many, the findings in the report come as no surprise. Experts have long warned that

Ransomware attackers count institutions of all sizes among their targets,
While ransomware itself threatens financial institutions, banks also face a legal quandary when they potentially facilitate a payment related to ransomware, and it gets even more complicated when a ransom payment might end up in Russia.
While the U.S. government "strongly discourages the payment of cyber ransom or extortion demands" according to
"Such payments not only encourage and enrich malicious actors, but also perpetuate and incentivize additional attacks," the 2021 advisory from Fincen said. "Moreover, there is no guarantee that companies will regain access to their data or be free from further attacks themselves."